NADER ALHARBI
I'm a Penetration Tester
About Me
Cybersecurity enthusiast with a strong interest in penetration testing, red teaming, and ethical hacking.
Skilled in identifying and exploiting vulnerabilities to strengthen systems and networks.
Continuously learning and exploring new exploitation techniques.
Strong team player with a proactive approach to learning and problem-solving.
Dedicated to contributing effectively to the cybersecurity field while advancing technical expertise.

Education
Bachelor degree in Cybersecurity
University of Jeddah
Experience
Offensive Security Trainee - TAHAKOM
- Part of the penetration testing team performing high-production security assessments.
- Identified 35+ vulnerabilities, including critical findings across multiple environments.
- Contributed to technical security reports, including risk analysis and remediation guidance.
- Gained hands-on experience in testing using tools such as Burp Suite, Nmap, Metasploit, and other offensive security tools.
Cybersecurity Content Specialist - Synapse
Accomplishments
CVE-2025-39245
CSV Injection Vulnerability in some HikCentral Master Lite versions.
This could allow an attacker to inject executable commands via malicious CSV data.
Certifications
Professional certifications that enhanced my expertise and validated my skills in various domains.

Certified Red Team Professional (CRTP)
Issued by Altered Security
Key Topics and skills gained
• Active Directory (AD) Enumeration
• AD attacks
• ACLs Abuse
• AD Persistence
• Child to parent domain escalation
• Trust Attacks
• Forest privilege escalation
Web Application Penetration Tester eXtreme (eWPTX)
Issued by INE
Key Topics and skills gained
• Web Application Penetration Testing Methodology
• Web Application Reconnaissance
• Authentication Attacks
• Advanced Injection Vulnerabilities
• API Penetration Testing
• Server-Side Attacks
• Filter Evasion & WAF Bypass

Certified Professional Penetration Tester (eCPPT)
Issued by INE
Key Topics and skills gained
• Client-Side Attacks
• Web Application PT
• Network Penetration Testing
• Exploit Development
• Post-Exploitation
• Red Teaming and Active Directory Penetration Testing

Mobile Application Penetration Testing (eMAPT)
Issued by INE
Key Topics and skills gained
• Android and iOS Architecture
• Static and Dynamic Analysis
• Developing APK Exploits
• Reversing APKs
• Intercepting Web Requests
Junior Penetration Tester (PT1)
Issued by TryHackMe
Key Topics and skills gained
• Offensive security frameworks
• OWASP Top 10 vulnerabilities
• Privilege Escalation
• Report Writing
• Pentester Mindset
Certified Red Team Analyst (CRTA)
Issued by CWL
Key Topics and skills gained
• Red Team Methodologies
• Understanding of MITRE ATT&CK
• Internal & External Recon
• Perform Kerberos based attacks in fully patched Active Directory
• Pivoting and Lateral Movement Techniques

Certified Threat Hunting Professional (eCTHP)
Issued by INE
Key Topics and skills gained
• Threat hunting Methodologies
• Threat hunting using Splunk
• Threat hunting using ELK
• Memory-based threat hunting

Junior Penetration Tester (eJPT)
Issued by INE
Key Topics and skills gained
• Assessment Methodologies
• Host & Network Auditing
• Host & Network PT
• Web Application PT
Cybernetics ProLabs
Issued by Hack The Box
Key Topics and skills gained
• Web Application Attacks
• Kerberos Abuse
• Active Directory Enumeration
• Active Directory Exploitation
• Phishing
• Privilege Escalation
• Lateral Movement
• Evading Endpoint Protections

RastaLabs ProLabs
Issued by Hack The Box
Key Topics and skills gained
• Situational Awareness
• Active Directory Enumeration
• Active Directory Exploitation
• Phishing
• Password Cracking and Credential Theft
• Privilege Escalation
• Lateral Movement
• Evading Endpoint Protections
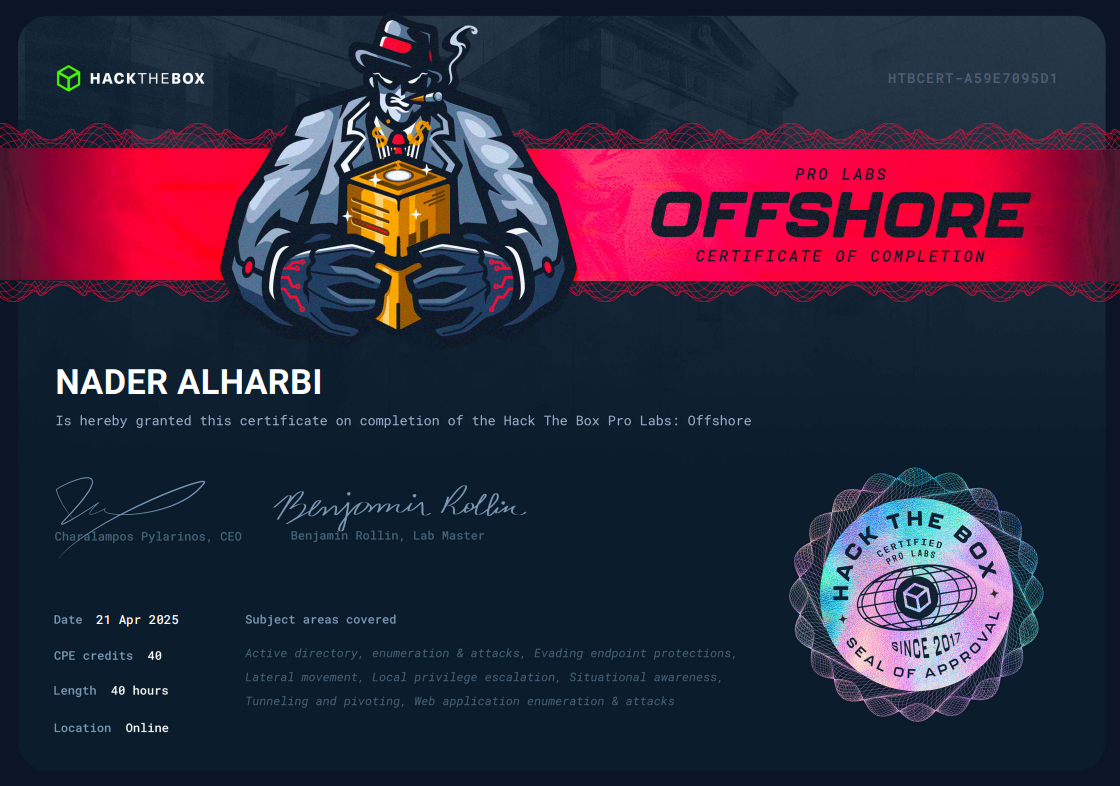
Offshore ProLabs
Issued by Hack The Box
Key Topics and skills gained
• Web Application Attacks
• Enumeration
• Exploiting Real-World Active Directory Flaws
• Local Privilege Escalation
• Lateral Movement and Crossing Trust Boundaries
• Evading Endpoint Protections
• Compromising all 5 Domains

Zephyr ProLabs
Issued by Hack The Box
Key Topics and skills gained
• Active Directory
• Red Teaming
• Enumeration
• ACLs Abuse
• Lateral movement and crossing trust boundaries
• Pivoting
• SQL attacks
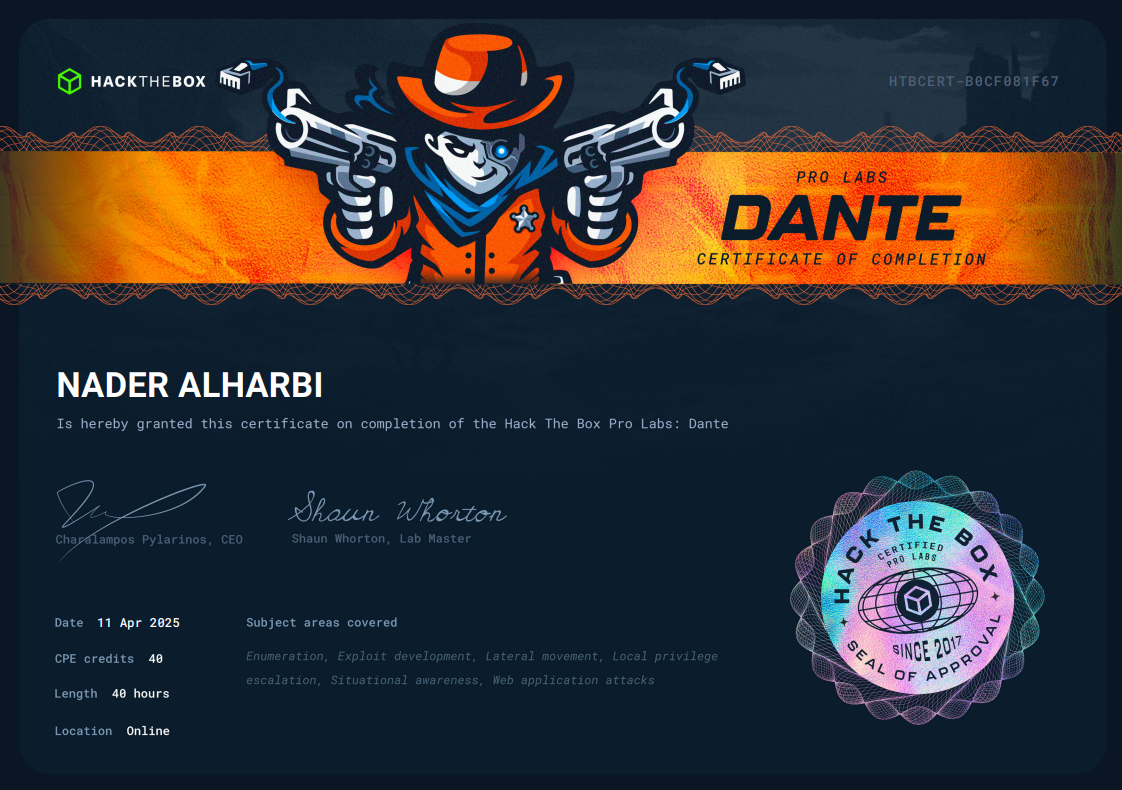
Dante ProLabs
Issued by Hack The Box
Key Topics and skills gained
• Enumerating networks and machines
• Exploiting numerous vulnerabilities
• Crafting custom payloads
• Lateral movement
• Pivoting
• Escalating privileges
Courses & Bootcamps
Continuous learning is key to staying ahead in the fast-evolving cybersecurity landscape. Here are some of the courses and bootcamps I've completed to enhance my skills.
TryHackMe
Top 1% of overall users
TryHackMe is a Cybersecurity Learning platform where I completed 100+ rooms ranging from cybersecurity basics to Penetration testing and red teaming
Cybersecurity Bootcamp
NCA & KAUST
An exceptional bootcamp experience where I advanced through three intensive stages, solidifying my skills and expanding my knowledge in the cybersecurity field.
Threat hunting Bootcamp
CyberHub
A comprehensive training program covering the eCTHP curriculum. I ranked among the top students and was awarded a voucher for the eCTHP certification
Web Application Penetration Testing Bootcamp
CyberHub
This bootcamp primarily focused on the eWPT and eWPTX certifications, significantly enhancing my skills in Web Application Penetration Testing.
Web Application Penetration Tester (eWPT)
INE
Even though I did not take the eWPT certifications I finished the course where I learned The basics of Web Pentesting
NCA & SITE
Cybersecurity Bootcamp
Fruitful bootcamp that explored certifications like Network+ and Security+, supported by hands-on SOC analysis and penetration testing simulations. We concluded the program with a practical exam demonstrating the skills acquired.
Active Directory Penetration Testing Bootcamp
CyberHub
This Bootcamp focused on Active Directory penetration testing life cycle. including topics like Active Directory Foundations, Breaching Active Directory, Enumerating, Lateral Movement, Persistence.
Mobile Application Penetration Testing Bootcamp
CyberHub
This Bootcamp initially was about the eMAPT Certificate. But, It went above and beyond the Certificate topics. Covering Advanced topics like Frida, Binary patching techniques, Bypassing certificate pinning, root and virtual machine checks, Frameworks like Flutter, Xamarin Forms, and React Native
Projects
Here are some of the projects I've worked on that showcase my skills and expertise. Click a project to view its demo video.

Google Chrome Password Stealer
This malware decrypts and steals passwords stored in Google Chrome, sending them to the attacker’s Command and Control (C2) server without detection from Windows Defender on Windows 10.

Subnet Scanner
This Python program identifies live hosts on a subnet, useful for penetration testers to locate active hosts.
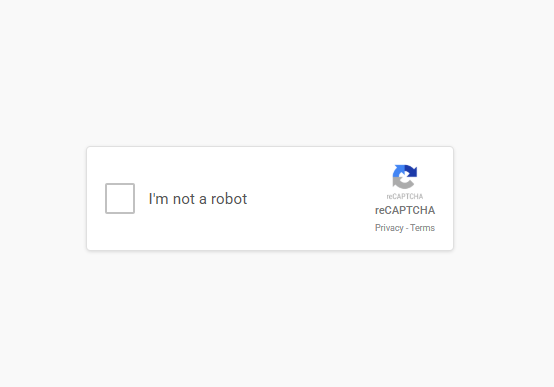
Fake CAPTCHA Attack Simulation
This demo replicates how threat actors use fake CAPTCHA pages to trick victims into executing malicious code. Designed to raise awareness, it highlights the importance of verifying website authenticity to prevent falling for such social engineering attacks.
Try Demo
NRcTwo
This is an IP-less Command and Control (C2) server I developed that leverages Telegram as the communication channel. The C2 framework includes multiple functionalities, such as:
• Gathering system information from the victim machine
• Executing commands on the victim machine
• Taking screenshots
• Retrieving public IP and location
• Persistence via startup apps